How to Avoid Sanctions Liability Following a Ransomware Attack

Matt Stankiewicz, Partner at The Volkov Law Group, joins us for an interesting post on ransomware and OFAC sanctions compliance. Matt can be reached at [email protected].
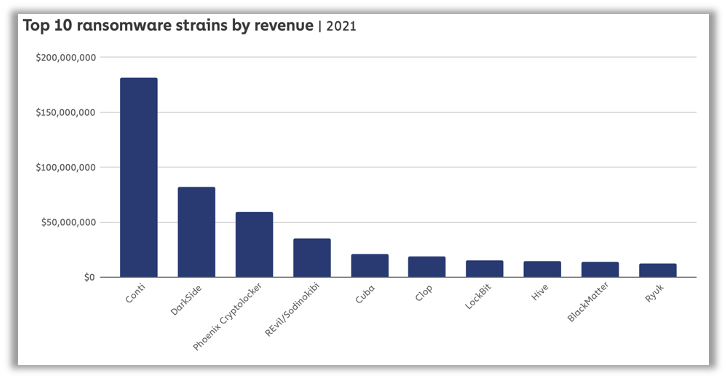
Ransomware attacks are on the rise and companies everywhere should be taking action to strengthen their cybersecurity defenses and resiliency to ensure their internal systems are able to withstand cybercrime attacks. Cybercriminals are exceedingly sophisticated, some groups even maintain staff spread throughout the world handling a variety of issues for the group. A recent leak of internal chat logs and other information from the prominent Conti cybercrime group revealed that they even have an HR department that scours resume databases throughout the world to identify candidates that might be able to provide value to the organization. Many of these organizations even hire out call centers in foreign countries to operate as the negotiators – they provide them with scripts and guidelines on how to negotiate and what terms to accept or reject. Some groups operate as what is known as ransomware-as-a-service, where they license out the use of their malicious code to users who inject it into corporate systems. Once installed, it runs automatically and splits payments between the creator and the licensee. A recent review by Chainalysis revealed some staggering revenues in the last year:
As if the data issues weren’t enough, these attacks present another potential pitfall – sanctions liability. For a refresher, OFAC administers and enforces economic sanctions programs primarily against countries, entities, groups, and individuals for various diplomatic reasons. The sanctions can be either comprehensive or selective and use the blocking of assets and trade restrictions to advance foreign policy and national security goals. U.S. persons are prohibited from engaging in transactions with sanctioned entities unless authorized by OFAC or expressly exempted by statute.
While Russia has made headlines lately with a variety of new sanctions programs, understand that one of the primary sanctions programs that President Biden is utilizing to punish Russia for its invasion is an executive order initially signed on April 15, 2021 – Executive Order 14024, Blocking Property With Respect To Specified Harmful Foreign Activities of the Government of the Russian Federation. Among other things, this Executive Order focused on “cyber-enabled activities” and targeted Russia’s notorious cybercrime community (which, as you can imagine, includes the troll farms and cyber propaganda arms that are responsible for interfering with elections). Additionally, President Obama previously signed two executive orders – 13694 and 13757 – which dealt exclusively with “malicious cyber-enabled activities.” Based on these authorities, and despite the supposed anonymity of these cybercriminals, the U.S. government still has a variety of resources at its disposal to identify the individuals behind the keyboards. As such, OFAC has already designated several individuals who have created and/or facilitated cybercrimes throughout the years. Even if the individuals are not identifiable, OFAC has sanctioned cybercriminal groups, including their related cryptocurrency wallet addresses and even the cryptocurrency exchanges they use to facilitate many of these transactions. In sum, OFAC is very active in the cybercrime space.
With regards to ransomware, OFAC has released specific guidance on the topic. OFAC warns that paying ransoms stemming from ransomware attacks can potentially violate sanctions regulations if those payments are made to sanctioned parties. OFAC emphasizes that violations are a strict liability offense. However, OFAC also recognizes various mitigating factors, such as the existence of a comprehensive sanctions compliance program and the adoption of cybersecurity defensive and resiliency measures – the latter being a “significant” mitigating factor. Additionally, OFAC stresses the need to report the cyberattack to relevant agencies. Voluntarily disclosing the situation to OFAC if it involves any potential sanctions concerns also can be a mitigating factor in any subsequent enforcement action.

This leads to potential issues for companies hit by these ransomware attacks. Do you pay the ransom in order to quickly recover your data and prevent its public release? Or do you avoid the payment, risk the loss of data and reputation, in order to avoid sanctions liability? It’s a tricky situation.
Despite the shadowy nature of these groups, very often there is far more information available than there may initially seem to be. For one, most – if not all – of these groups require payment in cryptocurrency. While many mistakenly believe crypto transactions are anonymous, they are the furthest thing from that. Rather, the blockchain keeps a record of all transactions, and the flow of funds can be tracked historically or in real time. For example, when conducting a review of a recent ransomware attack for a client, we engaged a reputable cryptocurrency forensic group to utilize data analytics to track the wallets and funds of the group at issue. Using these tools, we were able to follow the group’s funds on a short trip to a few very reputable exchanges, where they were likely cashed out into fiat. Knowing the funds were moved quickly into a KYC’ed exchange gave some solace that these groups were not subject to sanctions. Along with a variety of other tools and comprehensive due diligence, we were able to provide assurances to the client that this ransom could be safely paid without violating sanctions.
Paying the ransom is not the end of the battle, however. Even assuming the group holds up their end of the bargain (which is not guaranteed, but often they do comply since they know that keeps future ransom payments flowing), more problems can arise shortly thereafter. If a company is known to pay a ransom following an infection of their systems, then they are placed on a list that is sold around the dark web to other cybercriminal groups. This list is effectively a sales list of “hot leads.” Furthermore, with the rise of companies willing to insure against these ransom payments, that information will be included on the list and will only increase the willingness of other hacker groups to try and get a piece of the pie. Therefore, once attacked by ransomware, a company should consider conducting extensive remediation to ensure their systems can withstand a continued barrage of attacks.
To aid in this endeavor, the U.S. Government has provided a variety of resources to companies. The U.S. Cybersecurity & Infrastructure Security Agency (“CISA”), for example, provides free “hygiene” services to corporate systems to identify any glaring problems and weaknesses. CISA continues to release advisories to warn against the latest bugs and viruses as they’re identified, along with recommended security measures and mitigation.
















1 Response
[…] Source link […]